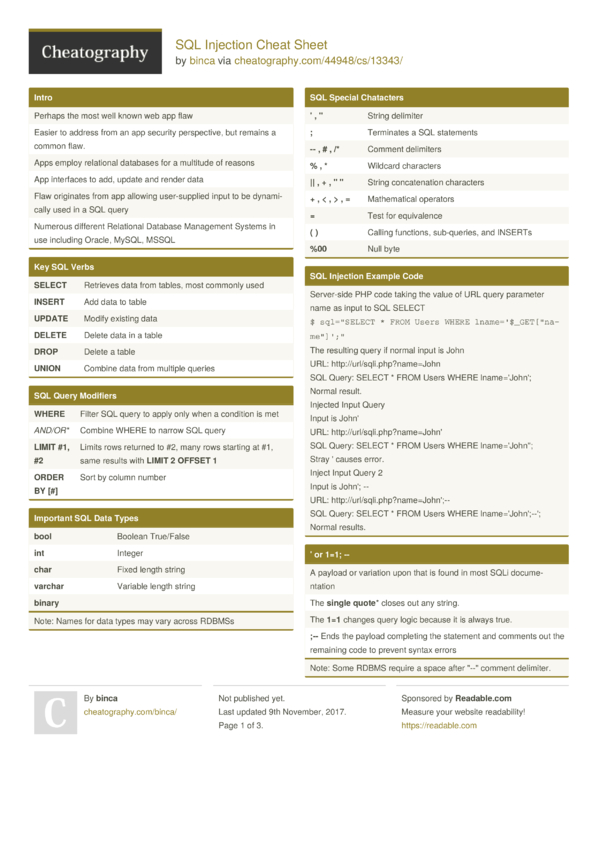
Sql Server Sql Injection Cheat Sheet
What is SQL Injection?
SQL injection is one of the most common web attack mechanisms utilized by attackers to steal sensitive data from organizations. While SQL Injection can affect any by using a compromised database server to attack to other systems on the same network
How to protect a web site or application from SQL Injection attacks
Developers can prevent SQL Injection vulnerabilities in web applications by utilizing parameterized database queries with bound, typed parameters and careful use of parameterized stored procedures in the database.
MSSQL Practical Injection Cheat Sheet - Perspective Risk MSSQL Practical Injection Cheat Sheet Following on from my MySQL Injection Practical Cheat Sheet here is the MSSQL version. As before, I will list the injections by their categories: union based, error based and inferential (time and boolean). The following script shows a simple SQL injection. The script builds an SQL query by concatenating hard-coded strings together with a string entered by the user: var Shipcity; ShipCity = Request.form ('ShipCity'); var sql = 'select. from OrdersTable where ShipCity = ' + ShipCity + '; The user is prompted to enter the name of a city. Pentestmonkey: Detailed SQL injection cheat sheets for penetration testers; Bobby Tables: The most comprehensible library of SQL injection defense techniques for many programming languages. Download the PDF version of the SQL injection Cheat Sheet. SQL INJECTION CHEAT SHEET Common SQL Injection Commands for Backend Databases MS-SQL Grab version @@version Users name FROM master.syslogins Tables.

This can be accomplished in a variety of programming languages including Java, .NET, PHP, and more.
Please consult the following resources for implementing parameterized database queries and preventing SQL Injection in your code base:
Additionally, developers, system administrators, and database administrators can take further steps to minimize attacks or the impact of successful attacks:
- Keep all web application software components including libraries, plug-ins, frameworks, web server software, and database server software up to date with the latest security patches available from vendors.
- Utilize the principle of least privilege when provisioning accounts used to connect to the SQL database. For example, if a web site only needs to retrieve web content from a database using SELECT statements, do not give the web site's database connection credentials other privileges such as INSERT, UPDATE, or DELETE privileges. In many cases, these privileges can be managed using appropriate database roles for accounts. Never allow your web application to connect to the database with Administrator privileges (the 'sa' account on Microsoft SQL Server, for instance).
- Do not use shared database accounts between different web sites or applications.
- Validate user-supplied input for expected data types, including input fields like drop-down menus or radio buttons, not just fields that allow users to type in input.
- Configure proper error reporting and handling on the web server and in the code so that database error messages are never sent to the client web browser. Attackers can leverage technical details in verbose error messages to adjust their queries for successful exploitation.
Is input filtering enough to stop SQL Injection?
A common misconception is that input filtering and escaping can prevent SQL Injection. While input filtering can help stop the most trivial of attacks, it does not fix the underlying vulnerability.
In many cases, input filtering can be evaded by attackers leaving your web application vulnerable despite attempts to, for example, deny-list certain characters on a web form.
SQL Injection vulnerability email notification from security@berkeley.edu
Security Contacts that receive a SQL Injection vulnerability notice are responsible for identifying and notifying any stakeholders about the SQL Injection attack including functional owners, developers, system administrators, and database administrators in order to determine the vulnerable and potentially compromised resources.
Immediate action must be taken to address any confirmed SQL Injection flaws discovered:
- Once a person responsible for coordinating remediation is identified, please respond to the notice so that Information Security and Policy can work directly with the coordinator to ensure full remediation
- Coordinate an investigation of potentially vulnerable web pages and resources amongst developers or other stakeholders
- A review of web, application, and database logs may reveal the point of vulnerability and source of attacks
- Develop a plan to remediate any confirmed SQL Injection flaws and prevent future attacks
Additionally, if your system stores, processes, or transmits sensitive data such as UC P2/3 or UC P4 data as described in the Berkeley Data Classification Standard, you should immediately reply to the security notice (to security@berkeley.edu) and notify the Information Security Office.
This post is a reference of my examples for processing JSON data in SQL Server. For more detailed explanations of these functions, please see my post series on JSON in SQL Server 2016:
Additionally, the complete reference for SQL JSON handling can be found at MSDN: https://msdn.microsoft.com/en-us/library/dn921897.aspx
Parsing JSON
Getting string JSON data into a SQL readable form.
ISJSON()
Checks to see if the input string is valid JSON.
JSON_VALUE()
Extracts a specific scalar string value from a JSON string using JSON path expressions.
Strict vs. Lax mode
If the JSON path cannot be found, determines if the function should return a NULL or an error message.
JSON_QUERY()
Returns a JSON fragment for the specified JSON path.
This is useful to help filter an array and then extract values with JSON_VALUE():
OPEN_JSON()
Returns a SQL result set for the specified JSON path. The result set includes columns identifying the datatypes of the parsed data.
Creating JSON
Creating JSON data from either strings or result sets.
FOR JSON AUTO

Automatically creates a JSON string from a SELECT statement. Quick and dirty. Hdd regenerator bootable iso.
FOR JSON PATH
Sonny with a chance games so sketchy disney channel. Formats a SQL query into a JSON string, allowing the user to define structure and formatting.
Modifying JSON
Valentino rock n rose perfume boots. Updating, adding to, and deleting from JSON data.
JSON_MODIFY()
Allows the user to update properties and values, add properties and values, and delete properties and values (the delete is unintuitive, see below).
Modify:
Add:
Delete property:
Delete from array (this is not intuitive, see my Microsoft Connect item to fix this: https://connect.microsoft.com/SQLServer/feedback/details/3120404/sql-modify-json-null-delete-is-not-consistent-between-properties-and-arrays )
SQL JSON Performance Tuning
SQL JSON functions are already fast. Adding computed columns and indexes makes them extremely fast.
Computed Column JSON Indexes
JSON indexes are simply regular indexes on computed columns.
Add a computed column:
Add an index to our computed column:
Microsoft Sql Server 2012 Sql Injection Cheat Sheet
Performance test:
