Firewall CyberGuard
Korg d1600 specs. An Introduction to Firewalls


Overview of Securing Networks and Systems
Firewall The CyberGuard SG appliance is equipped with a fully featured, stateful firewall. The firewall allows you to control both incoming and outgoing access, so that PCs on local networks can have tailored Internet access facilities while being shielded from malicious attacks from external networks. Firewall CyberGuard provides a stateful firewall with top-tier enterprise features such as Geo-IP blocking and continually updated threat intelligence feeds. Utilizing the Geo-IP blocking you can choose to block traffic to specific countries with which you do not do business. CyberGuard has threat. Firewall The CyberGuard SG appliance is equipped with a fully featured, stateful firewall. The firewall allows you to control both incoming and outgoing access, so that PCs on local networks can have tailored Internet access facilities while being shielded from malicious attacks from external networks. CYBERGUARD CyberGuard Server The CyberGuard elite enterprise server can sit at a network chokepoint and take real-time action against threats. The server supports 10G networks and provides firewall, intrusion detection, DNS security and many other features to protect your network. CYBER PROTECTION Contact us for more information contact.
Securing networks and computer systems is a complex problem. There is no one technology that will completely secure any network or computer system. Some of the different technologies used to secure networks and computer systems, and their functions, include:
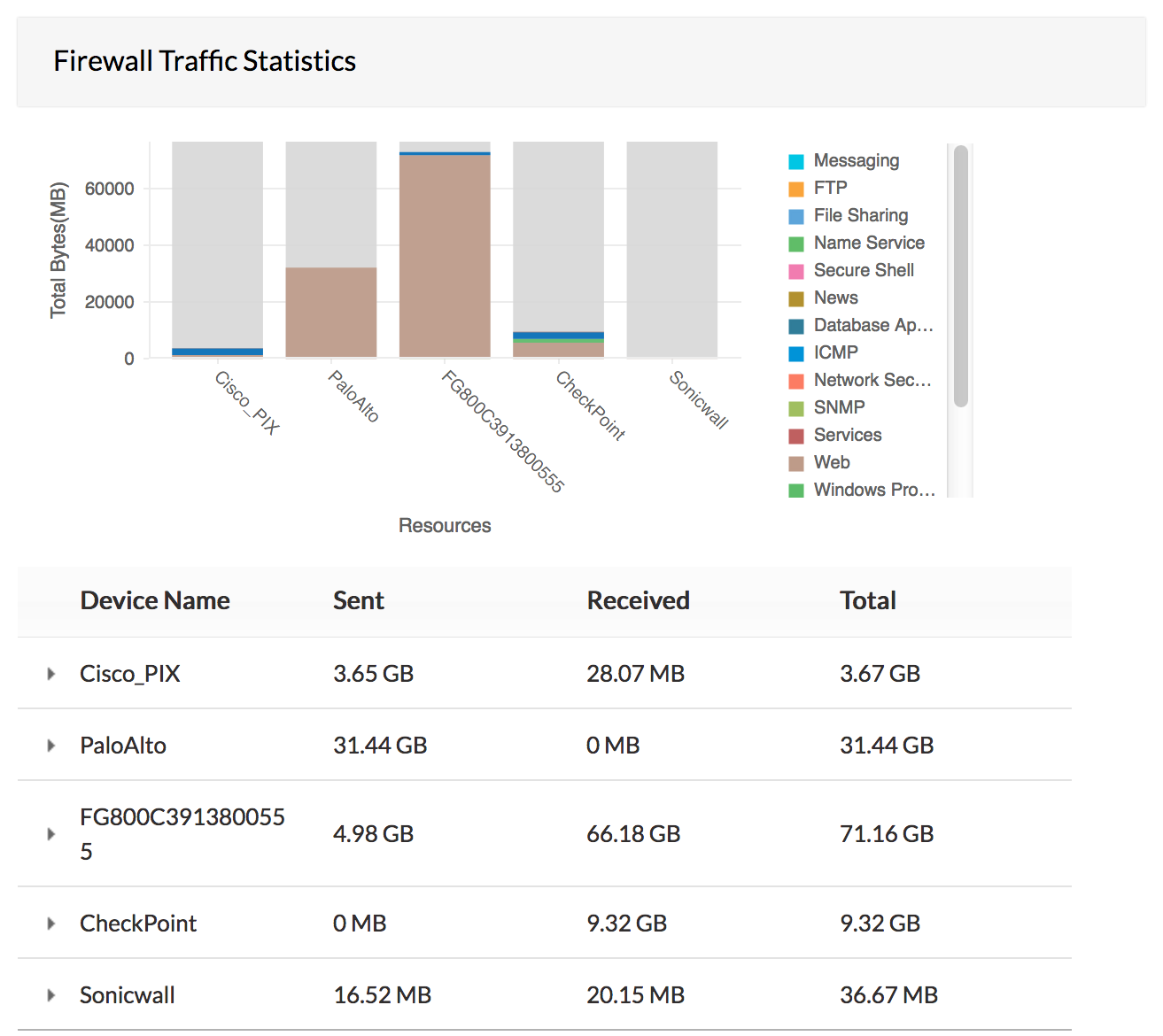
Cyberguard Firewall Vpn Sg300

Encryption is used to ensure the privacy of data and communications. When a file is encrypted, it becomes unreadable to those who do not have the key for decrypting it. PGP encryption is an example of encryption used to provide privacy for email communication. Virtual Private Networks (VPNs) use encryption to provide privacy for communication tunnels created through a public network, such as the Internet. Encryption can also be used to protect the files stored on an individual computer. Encryption can be used to protect the privacy of data that is stored on a particular computer, or data that is being transferred through a communication channel --- but cannot be used to prevent or detect attacks against networks or computers.
Virus Checkers are software (programs) used to scan files and processes on a computer for signatures, or patterns, associated with known malware such as viruses, trojan horses, or worms. Once a file or process has been identified as containing a known signature, the virus checker software can attempt to remove the file or to move it to an identified location (quarantine) so that the user or system administrator can take further action, if necessary. Virus checkers are used to protect against malicious software on an individual computer, or host.
Spyware Detection Software is used to scan files and configuration settings on a computer system to look for situations that may indicate the presence of spyware. Many of the indications reported by spyware detection software may not really be a problem and the user needs to have a pretty good idea of what is 'normal' for the particular computer system in order to determine whether a particular report requires corrective action. Like virus checkers, spyware detection software is used for protection on an individual computer, or host.
Firewalls are used to control the flow of traffic in a network, or to/from a particular host. Firewalls are used to prevent or reduce the probability of attacks against a network or host from occurring, but they cannot detect an attack in progress.
Intrusion Detection Systems (IDSs) are used like burglar alarms to detect indications that an attack is in progress, or has occurred, against a network or an individual host --- but they cannot prevent an attack occurring. However, like burglar alarms, using an intrusion detection system may deter attacks, since if attackers know that you are using an IDS, they may decide that they don't want to take the chance of being detected if they attack your system.
Cyberguard Firewall
What is a Firewall and Why Do We Care?
Firewalls serve several different purposes. Within a network, they can be used to manage the flow of traffic and improve network performance by limiting the volume of traffic in different parts of the network. From the perspective of security, firewalls are generally used to provide a boundary between a public network, such as the Internet, and a private network, such as a home or corporate network. Firewalls can be individual computers that run 'personal' firewall software, such as ZoneAlarm, or specialized, dedicated devices that operate within a network environment, such as Cisco PIX firewalls. Firewalls can also be dedicated computers that run firewall software in the network environment. Some examples of different firewall architectures are illustrated below.

